Integrate gitStream with Jit
Included with gitStream Core Functionality
This integration is part of gitStream core functionality, and requires no additional configuration.
Automation Examples
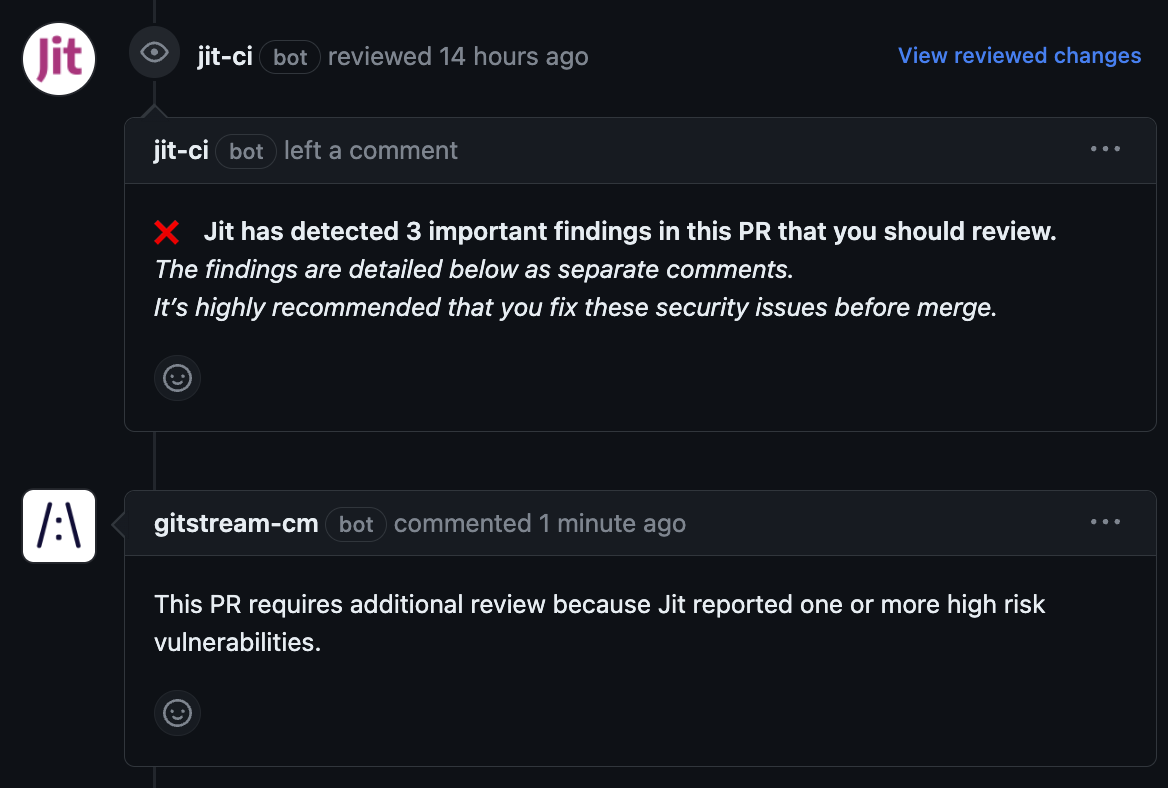
Review Jit Security Alerts
Manage review assignment for high and medium risk Jit security alerts.
Configuration Description
**Review Jit High Alerts**
* Conditions (all must be true):
* Jit reports one or more high vulnerabilities for the PR
* Automation Actions:
* Require a review from the organization’s security team.
* Require 2 reviewers.
* Post a comment explaining why this action was taken.
**Review Jit Medium Alerts**
* Conditions (all must be true):
* Jit reports one or more medium vulnerabilities for the PR
* Automation Actions:
* Require 2 reviewers
* Post a comment explaining why this action was taken.
Review Jit Security Alerts
# -*- mode: yaml -*-
manifest:
version: 1.0
automations:
review_jit_high_alerts:
if:
- {{ jit.metrics.HIGH > 0 }}
run:
- action: require-reviewers@v1
args:
reviewers: [my-organization/security-team]
- action: set-required-approvals@v1
args:
approvals: 2
- action: add-comment@v1
args:
comment: |
This PR requires additional review because Jit reported one or more high risk vulnerabilities.
review_jit_medium_alerts:
if:
- {{ jit.metrics.MEDIUM > 0 }}
run:
- action: set-required-approvals@v1
args:
approvals: 2
- action: add-comment@v1
args:
comment: |
This PR requires additional reviewers because Jit reported one or more medium risk vulnerabilities.
jit: {{ pr | extractJitFindings }}
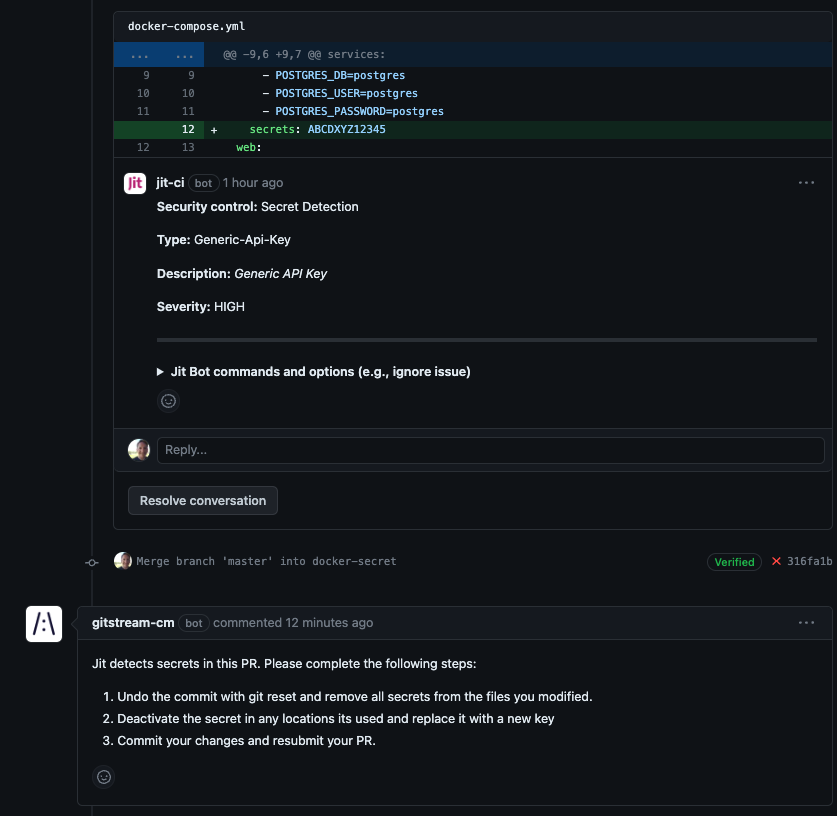
Review Jit Secret Detection
Close PRs where Jit detects a secret and post a comment explaining steps to remedy the situation.
Configuration Description
Conditions (all must be true):
- Jit detects a secret in the PR.
Automation Actions:
- Close the PR
- Post a comment explaining why this action was taken and to outline the necessary steps to remedy the situation.
Review Jit Security Control
# -*- mode: yaml -*-
manifest:
version: 1.0
automations:
review_jit_secret:
if:
- true
- {{ jit.vulnerabilities | match(attr='security_control', term='Secret Detection') | some }}
run:
- action: add-comment@v1
args:
comment: |
Jit detects secrets in this PR. Please complete the following steps:
1. Undo the commit with git reset and remove all secrets from the files you modified.
2. Deactivate the secret in any locations its used and replace it with a new key
3. Commit your changes and resubmit your PR.
- action: close@v1
jit: {{ pr | extractJitFindings }}
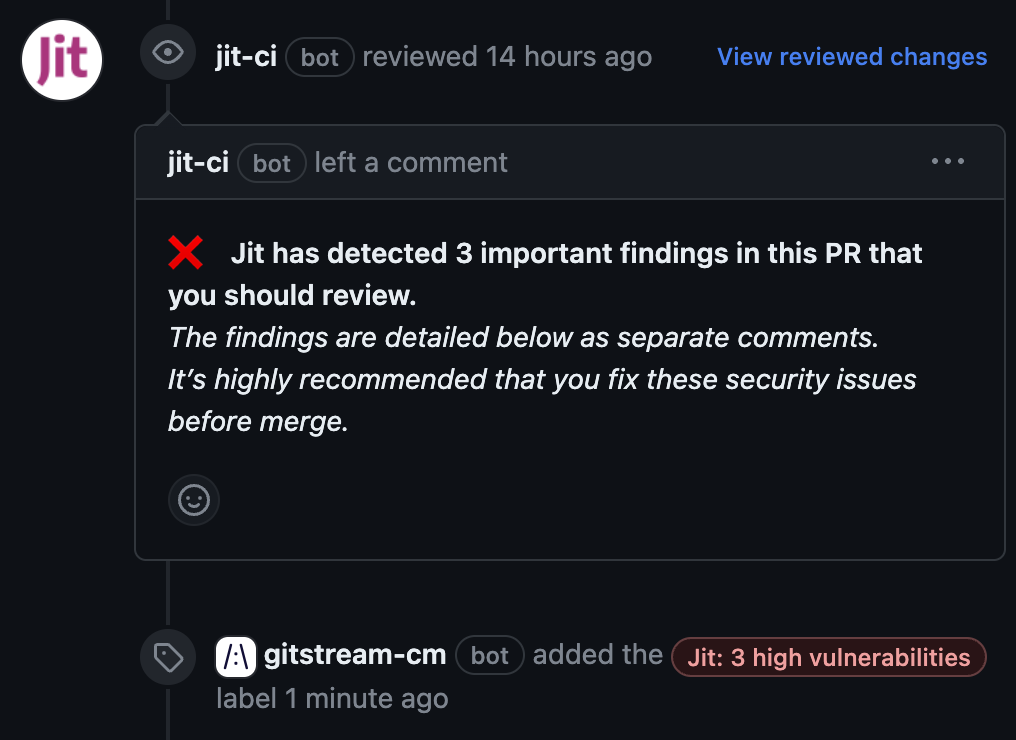
Label Jit Alerts
Label the number of high, medium, and low risk vulnerabilities Jit reports for PRs.
Configuration Description
Conditions (all must be true):
- Jit reports one or more high, medium, or low risk security vulnerabilities for the PR.
Automation Actions:
- Apply labels to indicate the number of each type of vulnerability
Label Jit Alerts
# -*- mode: yaml -*-
manifest:
version: 1.0
automations:
{% for item in reports %}
label_jit_{{ item.name }}:
if:
- {{ item.count > 0}}
run:
- action: add-label@v1
args:
label: 'Jit: {{ item.count }} {{ item.name }} vulnerabilities'
color: {{ colors.red if (item.name == 'high') else (colors.orange if (item.name == 'medium' ) else colors.yellow) }}
{% endfor %}
jit: {{ pr | extractJitFindings }}
reports:
- name: high
count: {{ jit.metrics.HIGH }}
- name: medium
count: {{ jit.metrics.MEDIUM }}
- name: low
count: {{ jit.metrics.LOW }}
colors:
red: 'b60205'
orange: 'd93f0b'
yellow: 'fbca04'
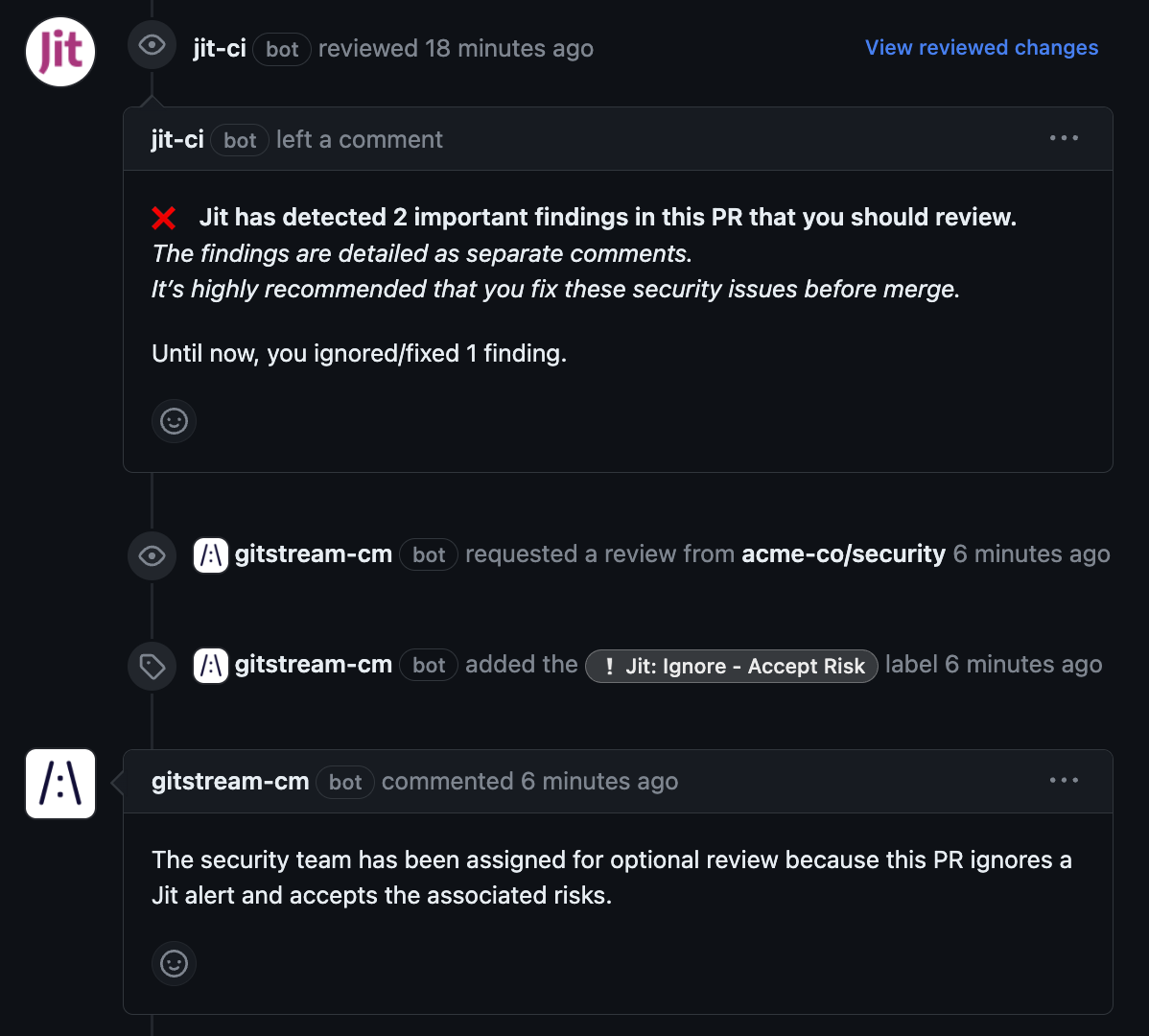
Review Jit Ignore and Accept
Notify your Security team when someone ignores a Jit vulnerability report and accepts the risk.
Configuration Description
Conditions (all must be true):
- Someone ignores and accepts a Jit finding
Automation Actions:
- Request review from the organization’s security team.
- Label the PR to indicate someone accepted the risk of a Jit security alert.
- Post a comment explaining why this action was taken.
Review Jit Ignore and Accept
# -*- mode: yaml -*-
manifest:
version: 1.0
automations:
review_jit_ignore_accept:
if:
- {{ pr.conversations | reject(attr='commenter', term='jit-ci') | filter(attr='content', term='#jit_ignore_accept') | some }}
run:
- action: add-reviewers@v1
args:
reviewers: [my-organziation/security]
- action: add-label@v1
args:
label: '❕ Jit: Ignore - Accept Risk'
- action: add-comment@v1
args:
comment: |
The security team has been assigned for optional review because this PR ignores a Jit alert and accepts the associated risks.
jit: {{ pr | extractJitFindings }}
Additional Resources
gitStream is a workflow automation tool that enables you to use YAML configuration files to optimize your code review process. Add context to PRs, find code experts for reviews, and automate the merge process to maximize developer productivity.
Learn More about how gitStream Works.
More Automations can be found on the Automation Library and Integrations pages.