Integrate gitStream with SonarCloud
Included with gitStream Core Functionality
This integration is part of gitStream core functionality, and requires no additional configuration.
Automation Examples
Approve Sonar Clean Code
Approve PRs that pass SonarCloud's quality gate.
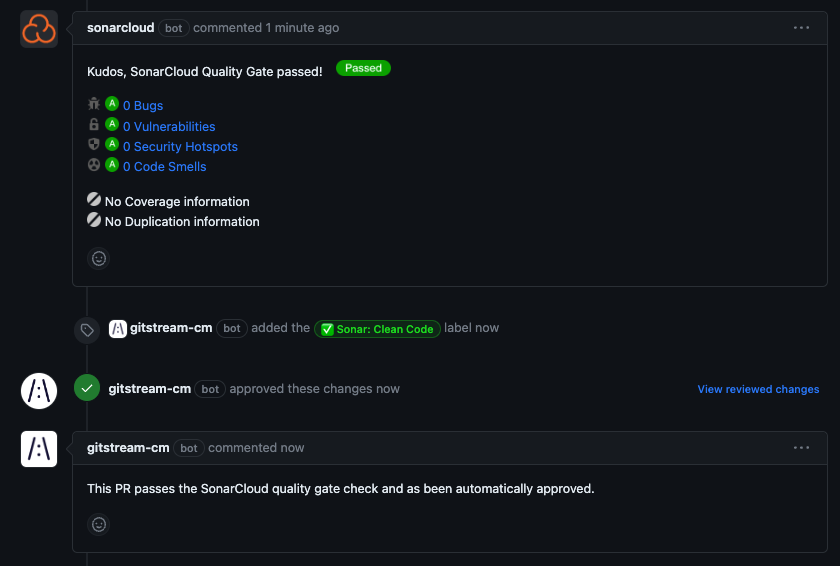
Configuration Description
Conditions (all must be true):
- SonarCloud reports an 'A' rating for vulnerabilities, bugs, security hotspots, and code smells.
- There is no duplicated code.
Automation Actions:
- Apply a
Sonar: Clean Codelabel to the PR. - Approve the PR.
- Post a comment that explains why the PR was approved.
Aprove Sonar Clean Code
# -*- mode: yaml -*-
manifest:
version: 1.0
automations:
approve_sonar_clean_code:
if:
- {{ sonar.bugs.rating == 'A' }}
- {{ sonar.code_smells.rating == 'A' }}
- {{ sonar.vulnerabilities.rating == 'A' }}
- {{ sonar.security_hotspots.rating == 'A' }}
- {{ sonar.duplications == null or sonar.duplications == 0 }}
run:
- action: add-label@v1
args:
label: '✅ Sonar: Clean Code'
color: {{ colors.green }}
- action: approve@v1
- action: add-comment@v1
args:
comment: |
This PR passes the SonarCloud quality gate check and as been automatically approved.
sonar: {{ pr | extractSonarFindings }}
colors:
green: '0e8a16'
Label SonarCloud Quality Reports
Label the number of bugs, vulnerabilities, security hotspots, and code smells reported by SonarCloud.
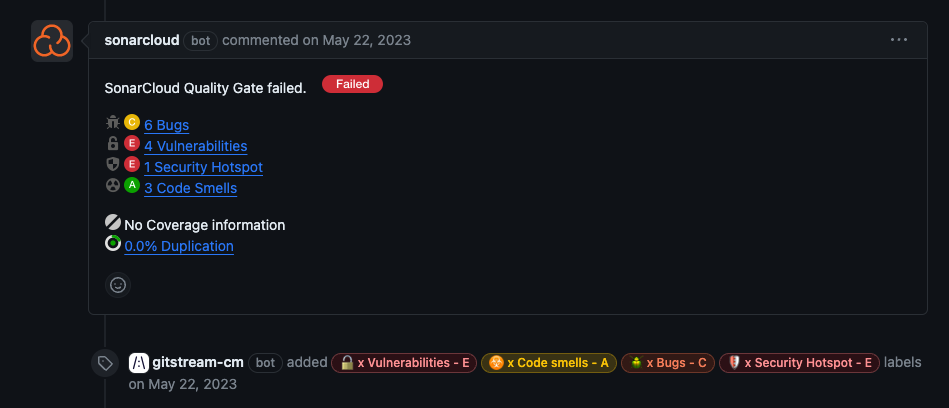
Configuration Description
Conditions (all must be true):
- There is at least one vulnerability, code smell, security hotspot, or bug reported by SonarCloud. Uses the
extractSonarFindingsfilter function
Automation Actions:
- Apply color-coded labels to indicate the number of vulnerabilities, code smells, security hotspots, and bugs.
Label SonarCloud Quality Reports
# -*- mode: yaml -*-
manifest:
version: 1.0
automations:
{% for item in reports %}
label_sonar_{{ item.name }}:
if:
- {{ item.count > 0}}
run:
- action: add-label@v1
args:
label: '{{ item.icon }} sonar:{{ item.name }}-{{ item.rating }}'
color: {{ colors.red if (item.rating == 'E' or item.rating == 'D') else (colors.orange if (item.rating == 'C' ) else colors.yellow) }}
{% endfor %}
sonar: {{ pr | extractSonarFindings }}
reports:
- name: vulnerabilities
count: {{ sonar.vulnerabilities.count }}
icon: 🔓
rating: {{ sonar.vulnerabilities.rating }}
- name: code smells
count: {{ sonar.code_smells.count }}
icon: ☣️
rating: {{ sonar.code_smells.rating }}
- name: security hotspots
count: {{ sonar.security_hotspots.count }}
icon: 🛡️
rating: {{ sonar.security_hotspots.rating }}
- name: bugs
count: {{ sonar.bugs.count }}
icon: 🪲
rating: {{ sonar.bugs.rating }}
colors:
red: 'b60205'
orange: 'd93f0b'
yellow: 'fbca04'
Review Sonar Duplications
Request changes when Sonar reports an excessive level of duplicated code.
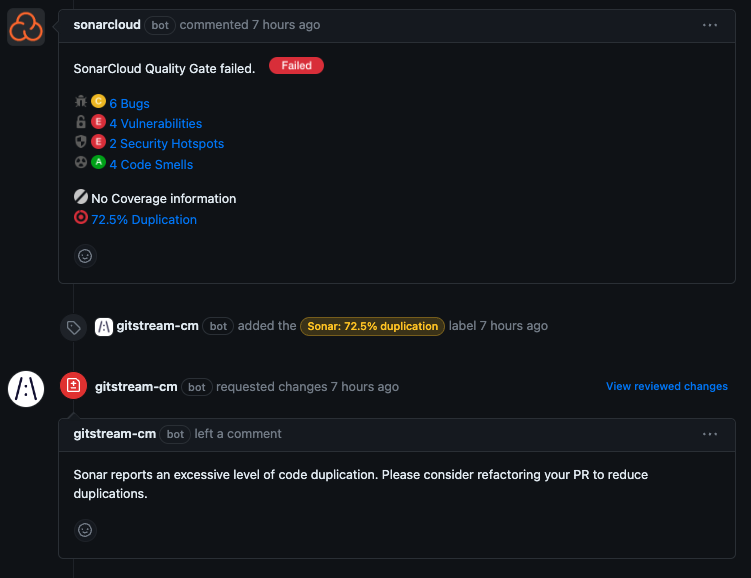
Configuration Description
Conditions (all must be true):
- The PR contains more than 3% duplicated code.
Automation Actions:
- Apply a label that indicates how much duplicated code Sonar detected.
- Request changes and post a comment explaining why.
Review Sonar Duplications
# -*- mode: yaml -*-
manifest:
version: 1.0
automations:
review_sonar_duplications:
if:
- {{ sonar.duplications > 3 }}
run:
- action: add-label@v1
args:
label: 'Sonar: {{ sonar.duplications}}% duplication'
color: {{ colors.yellow }}
- action: request-changes@v1
args:
comment: |
Sonar reports an excessive level of code duplication. Please consider refactoring your PR to reduce duplications.
sonar: {{ pr | extractSonarFindings }}
colors:
yellow: 'fbca04'
Review Sonar Security Alerts
Additional Resources
gitStream is a workflow automation tool that enables you to use YAML configuration files to optimize your code review process. Add context to PRs, find code experts for reviews, and automate the merge process to maximize developer productivity.
Learn More about how gitStream Works.
More Automations can be found on the Automation Library and Integrations pages.